A window manager that wishes to place constraints on the sizes of icon pixmaps and/or windows should place a property called WM_ICON_SIZE on the root. The contents of this property are listed in the following table.
| Field | Type | Comments |
| min_width | CARD32 | The data for the icon size series |
| min_height | CARD32 | |
| max_width | CARD32 | |
| max_height | CARD32 | |
| width_inc | CARD32 | |
| height_inc | CARD32 |
From the client's point of view, the window manager will regard each of the client's top-level nonoverride-redirect windows as being in one of three states, whose semantics are as follows:
In fact, the window manager may implement states with semantics other than those described above. For example, a window manger might implement a concept of "inactive" state in which an infrequently used client's window would be represented as a string in a menu. But this state is invisible to the client, which would see itself merely as being in IconicState.
Newly created top-level windows are in the Withdrawn state. Once the window has been provided with suitable properties, the client is free to change its state as follows:
Only the client can effect a transition into or out of the Withdrawn state. Once a client's window has left the Withdrawn state, the window will be mapped if it is in the Normal state and the window will be unmapped if it is in the Iconic state. Reparenting window managers must unmap the client's window when it is in the Iconic state, even if an ancestor window being unmapped renders the client's window unviewable. Conversely, if a reparenting window manager renders the client's window unviewable by unmapping an ancestor, the client's window is by definition in the Iconic state and must also be unmapped.
When changing the state of the window to Withdrawn, the client must (in addition to unmapping the window) send a synthetic UnmapNotify event by using a SendEvent request with the following arguments:
| Argument | Value |
| destination: | The root |
| propagate: | False |
| event-mask: | (SubstructureRedirect|SubstructureNotify) |
| event: an UnmapNotify with: | |
event: |
The root |
window: |
The window itself |
from-configure: |
False |
When a client withdraws a window, the window manager will then update or remove the WM_STATE property as described in Section 3.4.1.3.1. Clients that want to re-use a client window (e.g. by mapping it again or reparenting it elsewhere) after withdrawing it must wait for the withdrawal to be complete before proceeding. The preferred method for doing this is for client to wait for the window manager to update or remove the WM_STATE property.
(Note: Earlier versions of these conventions prohibited clients from reading the WM_STATE property. Clients operating under to earlier conventions used the technique of tracking ReparentNotify events to wait for the top-level window to be reparented back to the root window. This R still a valid technique: however. h works only for reparenting window managers. and the WM_STATE technique is to be preferred. )
If the transition is from the Normal to the Iconic state, the client should send a ClientMessage event to the root with:
Over values of data[0] are reserved for future extensions to these conventions. The parameters of the SendEvent request should be those described for the synthetic UnmapNotify event.
Clients can resize and reposition their top-level windows by using the ConfigureWindow request. The attributes of the window that Can be altered with this request are as follows:
The coordinate system in which the location is expressed is that of the root (irrespective of any reparenting that may have occurred). The border width to be used and win_gravity position hint to be used are those most recently requested by the client. Client configure requests are interpreted by the window manager in the same manner as the initial window geometry mapped from the Withdrawn state, as described in Section 3.4.1.2.3. Clients must be aware that there is no guarantee that the window manager will allocate them the requested size or location and must be prepared to deal with any size and location. If the window manager decides to respond to a ConfigureRequest request by:
The general rule is that coordinates in real ConfigureNotify events are in the parent's space; in synthetic events, they are in the root space.
Clients should be aware that their borders may not be visible. Window managers are free to use reparenting techniques to decorate client's top-level windows with borders containing titles, controls, and other details to maintain a consistent look-and-feel. If they do, they are likely to override the client's attempts to set the border width and set it to zero. Clients, therefore, should not depend on the top-level window's border being visible or use it to display any critical information. Other window managers will allow the top-level windows border to be visible.
Clients that change their position in the stack must be aware that they may have been reparented, which means that windows that used to be siblings no longer are. Using a nonsibling as the sibling parameter on a ConfigureWindow request will cause an error.
Clients that must position themselves in the stack relative to some window that was originally a sibling must do the Configure Window request (in case they are running under a nonreparenting window manager), be prepared to deal with a resulting error, and then follow with a synthetic ConfigureRequest event by invoking a SendEvent request with the following arguments:
| Argument | Value |
| destination: | The root |
| propagate: | False |
| event-mask: | (SubstructureRedirect|SubstructureNotify) |
| event: a ConfigureRequest | |
| with: | |
| event: | The root |
| window: | The window itself |
| ... | Other parameters from the ConfigureWindow request |
Window managers are in any case free to position windows in the stack as they see fit, and so clients should not rely on receiving the stacking order they have requested. Clients should ignore the above-sibling field of both real and synthetic ConfigureNotify events received on their top-level windows because this field may not contain useful information.
The attributes that may be supplied when a window is created may be changed by using the ChangeWindowAttributes request. The window attributes are listed in the following table.
| Attribute | Private to Client |
| Background pixmap | Yes |
| Background pixel | Yes |
| Border pixmap | Yes |
| Border pixel | Yes |
| Bit gravity | Yes |
| Window gravity | No |
| Backing-store hint | Yes |
| Save-under hint | No |
| Event mask | No |
| Do-Not-propagate mask | Yes |
| Override-redirect flag | No |
| Colormap | Yes |
| Cursor | Yes |
Most attributes are private to the client and will never be interfered with by the window manager. For the attributes that are not private to the client:
There are four models of input handling:
The four input models and the corresponding values of the input field and the presence or absence of the WM TAKE_FOCUS atom in the WM_PROTOCOLS property are listed in the following table:
| Input Model | Input Field | WM_TAKE_FOCUS |
| No Input | False | Absent |
| Passive | True | Absent |
| Locally Active | True | Present |
| Globally Active | False | Present |
Passive and Locally Active clients set the input field of WM_HINTS to True, which indicates that they require window manager assistance in acquiring the input focus. No Input and Globally Active clients set the input field to False, which requests that the window manager not set the input focus to their top-level window.
Clients that use a SetInputFocus request must set the time field to the timestamp of the event that caused them to make the attempt. This cannot be a FocusIn event because they do not have timestamps. Clients may also acquire the focus without a corresponding EnterNotify. Note that clients must not use CurrentTime in the time field.
Clients using the Globally Active model can only use a SetInputFocus request to acquire the input focus when they do not already have it on receipt of one of the following events:
In general, clients should avoid using passive-grabbed key events for this purpose, except when they are unavoidable (as, for example, a selection tool that establishes a passive grab on the keys that cut, copy, or paste).
The method by which the user commands the window manager to set the focus to a window is up to the window manager. For example, clients cannot determine whether they will see the click that transfers the focus.
Windows with the atom WM_TAKE_FOCUS in their WM_PROTOCOLS property may receive a ClientMessage
event from the window manager (as described in Section 3.4.2.8)
with WM_TAKE_FOCUS in their data[0] field and a valid timestamp (i.e. not Current Time) in
its data[1] field. If they want the focus, they should respond with a SetInputFocus
request with its window field set to the window of their that last had the input focus or
their "default input window," and the time field set to the timestamp in the
message. For further information, see Section 3.4.2.7.
SetInputFocus request with its window field set to the window of theirs that last
had the input focus or to their "default input window," and the time field set
to the timestamp in the message. For further information, see Section 3.4.2.7.
A client could receive WM_TAKE_FOCUS when opening from an icon or when the user has clicked outside the top-level window in an area that indicates to the window manager that it should assign the focus (for example, clicking in the headline bar can be used to assign the focus).
The goal is to support window managers that want to assign the input focus to a top-level window in such a way that the top-level window either can assign it to one of its subwindows or can decline the offer of the focus. For example, a clock or a text editor with no currently open frames might not want to take focus even though the window manager generally believes that clients should take the input focus after being deiconified or raised.
Clients that set the input focus need to decide a value for the revert-to field of the SetInputFocus request. This determines the behavior of the input focus if the window the focus has been set to becomes not viewable. The value can be any of the following:
Note that neither PointerRoot nor None is really safe to use.
A convention is also required for clients that want to give up the input focus. There is no safe value set for them to set the input focus to; therefore, they should ignore input material.
The window manager is responsible for installing and uninstalling colormaps on behalf of clients with top-level windows that the window manager manages.
Clients provide the window manager with hints as to which colormaps to install and uninstall. Clients must not install or uninstall or colormaps themselves (except under the circumstances noted below). When a client's top-level window gets the colormap focus (as a result of whatever colormap focus policy is implemented by the window manager), the window manager will ensure that one or more of the client's colormaps are installed.
Clients whose top-level windows and subwindows all use the same colormap should set its ID in the colromap field of the top-level window's attributes. They should not set a WM_COLORMAP_WINDOWS property on the top-level window. If they want to change the colormap, they should change the top-level window's colromap attribute. The window manager will track changes to the window's colormap attribute and install colormaps as appropriate.
Clients that create windows can use the value CopyFromParent to inherit their parent's colormap. Window managers will ensure that the root window's colormap field contains a colormap that is suitable for clients to inherit. In particular, the colormap will provide distinguishable colors for BlackPixel and WhitePixel.
Top-level windows that have subwindows or override-redirect pop-up windows whose colormap requirements differ from the top-level window should have a WM_COLORMAP_WINDOWS property. This property contains a list of IDs for windows whose colormaps the window manager should attempt to have installed when, in the course of its individual colormap focus policy, it assigns the colormap focus to the top-level window (see Section 3.4.1.2.8). The list is ordered by the importance to the client of having the colormaps installed. The window manager will track changes to this property and will track changes to the colormap attribute of the windows in the property.
If the relative importance of colormaps changes, the client should update the WM_COLORMAP_WINDOWS property to reflect the new ordering. If the top-level window does not appear in the list, the window manager will assume it to be of higher priority than any window in the list.
WM_TRANSIENT_FOR windows either can have their own WM_COLORMAP_WINDOWS property or can appear in the property of the window they are transient for, as appropriate.
Whenever possible, clients should use the mechanisms described above and let the window manager handle colormap installation. However, clients are permitted to perform colormap installation on their own while they have the pointer grabbed. A client performing colormap installation must notify the window manager prior to the first installation. When the client has finished its colormap installation, it must also notify the window manager. The client notifies the window manager by issuing a SendEvent request with the following arguments:
| Argument | Value |
| destination: | the root window of the screen on which the colormap is being installed |
| propagate: | False |
| event-mask: | ColormapChange |
| event:a ClientMessage with: | |
window: |
the root window, as above |
type: |
WM_COLORMAP_NOTIFY |
format: |
32 |
data[0]: |
the timestamp of the event that caused the client to start or stop installing colormaps |
data[l]: |
I if the client is starting colormap installation, 0 if the client is finished with colormap installation |
data[2]: |
reserved, must be zero |
data[3]: |
reserved, must be zero |
data[4]: |
reserved, must be zero |
This feature was introduced in version 2.0 of this document, and there will be a significant period of time before all window managers can be expected to implement this feature. Before using this feature, clients must check the compliance level of the window manager (using the mechanism described in Section 3.4.2.3) to verify that it supports this feature. This is necessary to prevent colormap installation conflicts between clients and older window managers.
Window managers should refrain from installing colormaps while a client has requested control of colormap installation. The window manager should continue to track the set of installed colormaps so that it can reinstate its colormap focus policy when the client has finished colormap installation.
This technique has race conditions that may result in the colormaps continuing to be installed even after a client has issued is notification message. For example, the window manager may have issued some InstallColormap requests that are not executed until after the client's SendEvent and InstallColormap requests, thus uninstalling the client's colormaps. If this occurs while the client sill has the pointer grabbed and before the client has issued the "finished" message, the client may reinstall the desired colormaps.
If a client fails to issue the "finished" message, the window manager may be left in a state where its colormap installation policy is suspended. Window manger implementors may want to implement a feature that resets colormap installation policy in response to a command from the user.
A client can hint to the window manager about the desired appearance of its icon by setting:
In the Iconic state, the window manager usually will ensure that:
Clients should observe the following conventions about their icon windows:
Window managers will differ as to whether they support input events to client's icon
windows;
most will allow the client to receive some subset of the keys and buttons.
Window managers will ignore any WM_NAME, WM_ICON_NAME, WM_NORMAL_HINTS, WM_HINTS, WM_CLASS, WM_TRANSIENT_FOR, WM_PROTOCOLS, or WM_COLORMAP_WINDOWS properties they find on icon windows. Session managers will ignore any WM_COMMAND or WM_CLIENT_MACHINE properties they find on icon windows.
Clients that wish to pop up a window can do one of three things:
Window managers are free to decide if WM_TRANSIENT_FOR windows should be iconified when the window they are transient for is. Clients displaying WM_TRANSIENT_FOR windows that have (or request to have) the window they are transient for iconified do not need to request that the same operation be performed on the WM_TRANSIENT_FOR window; the window manager will change its state if that is the policy it wishes to enforce.
A set of top-level windows that should be treated from the user's point of view as related (even though they may belong to a number of clients) should be linked together using the window_group field of the WM_HINTS structure.
One of the windows (that is, the one the others point to) will be the group leader and will carry the group as opposed to the individual properties. Window managers may treat the group leader differently from other windows in the group. For example, group leaders may have the full set of decorations, and other group members may have a restricted set.
It is not necessary that the client ever map the group leader; it may be a window that exists solely as a placeholder .
It is up to the window manager to determine the policy for treating the windows in a group. At present, there is no way for a client to request a group, as opposed to an individual, operation.
The window manager performs a number of operations on client resources, primarily on their top-level windows. Clients must not try to fight this but may elect to receive notification of the window manager's operations.
Clients must be aware that some window managers will reparent their top-level windows so that a window that was created as a child of the root will be displayed as a child of some window belonging to the window manager. The effects that this reparenting will have on the client are as follows:
Clients that want to be notified when they are reparented can select for StructureNotify events on their top-level window. They will receive a ReparentNotify event if and when reparenting takes place.
When a client withdraws a top-level window, the window manager will reparent it back to the root window if the window had been reparented elsewhere.
If the window manager reparents a client's window, the reparented window will be placed in the save-set of the parent window. This means that the reparented window will not be destroyed if the window manager terminates and will be remapped if it was unmapped. Note that this applies to all client windows the window manager reparents, including transient windows and client icon windows.
Clients must be aware that some window managers will arrange for some client requests to be intercepted and redirected. Redirected requests are not executed; they result instead in events being sent to the window manager, which may decide to do nothing, to alter the arguments, or to perform the request on behalf of the client.
The possibility that a request may be redirected means that a client cannot assume that any redirectable request is actually performed when the request is issued or is actually performed at all.
The requests that may be redirected are MapWindow, Configure Window, and Circulate-Window.
(Note: This is true even if the client set the hacking-store attribute to Always. The backing-store attribute is a only d him and the server may stop maintaining backing store contents at any time. )
This next example incorrectly assumes that the ConfigureWindow request is actually executed with the arguments supplied:
This technique does not guarantee correct operation. The user may have iconified the window by the time the SetInputFocus request reaches the server, still causing an error. Or, the window manger may decide to map the window into Iconic state, in which case the window will not be visible. This will delay the generation for the VisibilityNotify event indefinitely. Clients must be prepared to handle these cases.
A window with the override-redirect bit set is immune from redirection, but the bit should be set on top-level windows only in cases where other windows should be prevented from processing input while the override-redirect window is mapped (see Section 3.4.1.10) and while responding to ResizeRequest events (see Section 3.4.2.9).
Clients that have no non-Withdrawn top-level windows and that map an override-redirect toplevel window are taking over total responsibility for the state of the system. It is their responsibility to:
In effect, clients of this kind are acting as temporary window managers. Doing so is strongly discouraged because these clients will be unaware of the user interface policies the window manager is trying to maintain and because their user interface behavior is likely to conflict with that of less demanding clients.
If the window manager moves a top-level window without changing its size, the client will receive a synthetic ConfigureNotify event following the move that describes the new location in terms of the root coordinate space. Clients must not respond to being moved by attempting to move themselves to a better location.
Any real ConfigureNotify event on a top-level window implies that the window's position on the root may have changed, even though the event reports that the window's position in its parent is unchanged because the window may have been reparented. Note that the coordinates in the event will not, in this case, be directly useful.
The window manager will send these events by using a SendEvent request with the following arguments:
| Argument | Value |
| destination: | The client's window |
| propagate: | False |
| event-mask: | StructureNotify |
The client can elect to receive notification of being resized by selecting for StructureNotify events on its top-level windows. It will receive a ConfigureNotify event. The size information in the event will be correct, but the location will be in the parent window (which may not be the root).
The response of the client to being resized should be to accept the size it has been given and to do its best with it. Clients must not respond to being resized by attempting to resize themselves to a better size. If the size is impossible to work with, clients are free to request to change to the Iconic state.
A top-level window that is not Withdrawn will be in the Normal state if it is mapped and in the Iconic state if it is unmapped. This will be true even if the window has been reparented; the window manager will unmap the window as well as its parent when switching to the Iconic state.
The client can elect to be notified of these state changes by selecting for StructureNotify events on the top-level window. It will receive a UnmapNotify event when it goes Iconic and a MapNotify event when it goes Normal.
Clients that wish to be notified of their colormaps being installed or uninstalled should select for ColormapNotify events on their top-level windows and on any windows they have named in WM_COLORMAP_WINDOWS properties on their top-level windows. They will receive ColormapNotify events with the new field FALSE when the colormap for that window is installed or uninstalled.
Clients can request notification that they have the input focus by selecting for FocusChange events on their top-level windows; they will receive FocusIn and FocusOut events. Clients that need to set the input focus to one of their subwindows should not do so unless they have set WM_TAKE_FOCUS in their WM_PROTOCOLS property and have done one of the following:
Clients should not warp the pointer in an attempt to transfer the focus; they should set the focus and leave the pointer alone. For further information, see Section 3.6.2.
Once a client satisfies these conditions, it may transfer the focus to another of its windows by using the SetInputFocus request, which is defined as follows:
There is no way for clients to prevent themselves being sent ClientMessage events.
Top-level windows with a WM_PROTOCOLS property may be sent ClientMessage events specific to the protocols named by the atoms in the property (see Section 3.4.1.2.7). For all protocols, the ClientMessage events have the following
The remaining fields of the event, including the window field, are determined by the protocol.
These events will be sent by using a SendEvent request with the following arguments:
| Argument | Value |
| destination: | The client's window |
| propagate: | False |
| event-mask: | () empty |
| event: | As specified by the protocol |
Clients, usually those with multiple top-level windows, whose server connection must survive the deletion of some of their top-level windows, should include the atom WM_DELETE_WINDOW in the WM_PROTOCOLS property on each such window. They will receive a ClientMessage event as described above whose data[0] field is WM_DELETE_WINDOW.
Clients receiving a WM_DELETE_WINDOW message should behave as if the user selected "delete window" from a hypothetical menu. They should perform any confirmation dialog with the user and, if they decide to complete the deletion, should do the following:
If the user aborts the deletion during the confirmation dialog, the client should ignore the message. Clients are permitted to interact with the user and ask, for example, whether a file associated with the window to be deleted should be save or the window deletion should be cancelled. Clients are not required to destroy the window itself; the resource may be reused, but all associated state (for example, backing store) should be released.
If the client aborts a destroy and the user then selects DELETE WINDOW again, the window manager should start the WM_DELETE_WINDOW protocol again. Window managers should not use DestroyWindow requests on a window that has WM_DELETE_WINDOW in its WM_PROTOCOLS property.
Clients that choose not to include WM_DELETE_WINDOW in the WM_PROTOCOLS property may be disconnected from the server if the user asks for one of the client's top-level windows to be deleted.
Normal clients can use the redirection mechanism just as window managers do by selecting for SubstructureRedirect events on a parent window or ResizeRedirect events on a window itself. However, at most, one client per window can select for these events, and a convention is needed to avoid clashes.
In particular, clients that need to take some special action if they are resized can select for ResizeRedirect events on their top-level windows. They will receive a ResizeRequest event if the window manager resizes their window, and the resize will not actually take place. Clients are free to make what use they like of the information that the window manager wants to change their size, but they must configure the window to the width and height specified in the event in a timely fashion. To ensure that the resize will actually happen at this stage instead of being intercepted and executed by the window manager (and thus restarting the process3, the client needs temporarily to set override-redirect on the window.
If a window manager detects that a client is not obeying this convention, it is free to take whatever measures it deems appropriate to deal with the client.
For each screen they manage, window managers will acquire ownership of a selection named WM_Sn where n is the screen number, as described in Section 3.1.2.6. Window mangers should comply with the conventions for "Manager Selections" described in Section 3.2.8. The intent is for clients to be able to request a variety of information or services by issuing conversion requests on this selection. Window managers should support conversion of the following target on their manager selection:
| Atom | Type | Data Received |
| VERSION | INTEGER | Two integers, which are the major and minor release numbers (respectively) of the ICCCM with which the window manager complies. For this version of the ICCCM, the numbers are 2 and 015) |
The window manger properties are summarized in the following table (see also Section 14.1 of Xlib-C Language X Interface, Part II of the Xlib Programming Manual).
| Name | Type | Format | See Section |
| WM_CLASS | STRING | 8 | 3.4.1.2.5 |
| WM_CLIENT_MACHINE | TEXT | 3.4.1.2.9 | |
| WM_COLORMAP_WINDOWS | WINDOW | 32 | 3.4.1.2.8 |
| WM_HINTS | WM_HINTS | 32 | 3.4.1.2.4 |
| WM_ICON_NAME | TEXT | 3.4.1.2.2 | |
| WM_ICON_SIZE | WM_ICON_SIZE | 32 | 3.4.1.3.2 |
| WM_NAME | TEXT | 3.4.1.2.1 | |
| WM_NORMAL_HINTS | WM_SIZE_HINTS | 32 | 3.4.1.2.3 |
| WM_PROTOCOLS | ATOM | 32 | 3.4.1.2.7 |
| WM_STATE | WM_STATE | 32 | 3.4.1.3.1 |
| WM_TRANSIENT_FOR | WINDOW | 32 | 3.4.1.2.6 |
This section contains some conventions for clients that participate in session management. See X Session Management Protocol for further details. Clients that do not support this protocol cannot expect their window state (e.g. WM_STATE, position, size and stacking order) to be preserved across sessions.
Each session participant will obtain a unique client identifier (client-ID) from the session manager. The client must identify one top level window as the "client leader." This window must be created by the client. It may be in any state, including the Withdrawn state. The client leader window must have a SM_CLIENT_ID property, which contains the client-ID obtained from the session management protocol. That property must:
All top-level, non-transient windows created by a client on the same display as the client leader must have a WM_CLIENT_LEADER property. This property contains a window ID that identifies the client leader window. The client leader window must have a WM_CLIENT_LEADER property containing its own window ID (i.e. the client leader window is pointing to itself). Transient windows need not have a WM_CLIENT_LEADER property if the client leader can be determined using the information in the WM_TRANSIENT_FOR property. The WM_CLIENT_LEADER property must:
A client must withdraw all of its top level windows on the same display before modifying g either the WM_CLIENT_LEADER or the SM_CLIENT_ID property of its client leader window.
It is necessary that other clients be able to uniquely identify a window (across sessions) among all windows related to the same client-ID. For example, a window manager can require this unique ID to restore geometry information from a previous session, or a workspace manager could use it to restore information about which windows are in which workspace. A client may optionally provide a -WM_WINDOW_ROLE property to uniquely identify a window within the scope specified above. The combination of SM_CLIENT_ID and WM_WINDOW_ROLE can be used by other clients to uniquely identify a window across sessions.
If the WM_WINDOW_ROLE property is not specified on a top level window, a client that needs to uniquely identify that window will try to use instead the values of WM_CLASS and WM_NAME. If a client has multiple windows with identical WM_CLASS and WM_NAME properties, then it should provide a WM_WINDOW_ROLE property.
The client must set the WM_WINDOW_ROLE property to a string that uniquely identifies that window among all windows that have the same client leader window. The property must:
A window manger supporting session management must register with the session manager and obtain its own client-ID. The window manger should save and restore information such as the WM_STATE, the layout of windows on the screen, and their stacking order, for every client window that has a valid SM_CLIENT_ID property (on itself, or on the window named by WM_CLIENT_LEADER) and that can be uniquely identified. Clients are allowed to change this state during the first phase of the session checkpoint process. Therefore, window managers should request a second checkpoint phase and save clients' state only during that phase.
X Version 11 permits clients to manipulate a number of shared resources, for example, the input focus, the pointer, and colormaps. Conventions are required so that clients share resources in an orderly fashion.
Clients that explicitly set the input focus must observe one of two modes:
In general, clients should not warp the pointer. Window managers, however, may do so (for example, to maintain the invariant that the pointer is always in the window with the input focus). Other window managers may want to preserve the illusion that the user is in sole control of the pointer.
A client's attempt to establish a button or a key grab on a window will fail if some other client has already established a conflicting grab on the same window. The grabs, therefore, are shared resources, and their use requires conventions.
In conformance with the principle that clients should behave, as far as possible, when a window manager is running as they would when it is not, a client that has the input focus may assume that it can receive all the available keys and buttons.
In other words, window managers must provide some mechanism by which a client can receive events from every key and button (regardless of modifiers) unless and until the X Consortium registers some KeySyms as being reserved for window management functions. Currently, no KeySyms are registered for window management functions.
Even so, clients are advised to allow the key and button combinations used to elicit program actions to be modified, because some window managers may choose not to observe this convention or may not provide a convenient method for the user to transmit events from some keys.
In particular, this convention means that a window manager that wishes to establish a grab over the client's top-level window should either establish the grab on the root, or reparent the window and establish the grab on a proper ancestor. In some cases, a window manager may want to consume the event received, placing the window in a state where a subsequent such event will go to the client. Examples are:
More typically, a window manager should add to rather than replace the client's semantics for key+button combinations by allowing the event to be used by the client after the window manager is done with it. To ensure this, the window manager should establish the grab on the parent by using the following:
Then, the window manager should release the grab by using an AllowEvents request with the following specified:
In this way, the client will receive the events as if they had not been intercepted.
Obviously, these conventions place some constraints on possible user interface policies. There is a trade-off here between freedom for window managers to implement their user interface policies and freedom for clients to implement theirs. The dilemma is resolved by:
Section 3.4.1.8 prescribes conventions for clients to communicate with the window manager about their colormap needs. If your clients are DirectColor type applications, you should consult Section l 4.3 of Xlib-C Language X Interface for conventions connected with sharing standard colormaps. They should look for and create the properties described there on the root window of the appropriate screen.
The contents of the RGB_COLOR_MAP type property are as follows:
| Field | Type | Comments |
| colormap | COLORMAP | ID of the colormap described |
| red_max | CARD32 | Values for pixel calculations |
| red_mult | CARD32 | |
| green_max | CARD32 | |
| green_mult | CARD32 | |
| blue_max | CARD32 | |
| blue_mult | CARD32 | |
| base_pixel | CARD32 | |
| visual_id | VISUALID | Visual to which colormap belongs |
| kill_id | CARD32 | ID for destroying the resources |
When deleting or replacing an RGB_COLOR_MAP, it is not sufficient to delete the property; it is important to free the associated colormap resources as well. If kill_id is greater than one, the resources should be freed by issuing a KillClient request with kill_id as the argument. If kill_id is one, the resources should be freed by issuing a FreeColormap request with colormap as the colormap argument. If kill_id is zero, no attempt should be made to free the resources. A client that creates an RGB_COLOR_MAP for which the colormap resource is created specifically for this purpose should set kill_id to one (and can create more than one such standard colormap using a single connection). A client that creates an RGB_COLOR_MAP for which the colormap resource is shared in some way (for example, is the default colormap for the root window) should create an arbitrary resource and use its resource ID for kill_id (and should create no other standard colormaps on the connection).
During the connection handshake, the server informs the client of the default colormap for each screen. This is a colormap for the root visual, and clients can use it to improve the extent of colormap sharing if they use the root visual.
The X server contains a table (which is read by GetKeyboardMapping requests) that describes the set of symbols appearing on the corresponding key for each keycode generated by the server. This table does not affect the server's operations in any way; it is simply a database used by clients that attempt to understand the keycodes they receive. Nevertheless, it is a shared resource and requires conventions.
It is possible for clients to modify this table by using a ChangeKeyboardMapping request. In general, clients should not do this. In particular, this is not the way in which clients should implement key bindings or key remapping. The conversion between a sequence of keycodes received from the server and a string in a particular encoding is a private matter for each client (as it must be in a world where applications may be using different encodings to support different languages and fonts). See the Xlib reference manual for converting keyboard events to text.
The only valid reason for using a ChangeKeyboardMapping request is when the symbols written on the keys have changed as, for example, when a Dvorak key conversion kit or a set of APL keycaps has been installed. Of course, a client may have to take the change to the keycap on trust.
The following illustrates a permissible interaction between a client and a user:
| Client: | "You just started me on a server without a Pause key. Please choose a key to be the Pause key and press it now." |
| User: | Presses the Scroll Lock key |
| Client: | "Adding Pause to the symbols on the Scroll Lock key: Confirm or Abort." |
| User: | Confirms |
| Client: | Uses a ChangeKeyboardMapping request to add Pause to the keycode that already contains Scroll Lock and issues this request, "Please paint Pause on the Scroll Lock key. " |
If a client succeeds in changing the keyboard mapping table, all clients will receive MappingNotify (request==Keyboard) events. There is no mechanism to avoid receiving these events.
X Version 11 supports eight modifier bits of which three are preassigned to Shift, Lock, and Control. Each modifier bit is controlled by the state of a set of keys, and these sets are specified in a table accessed by GetModifierMapping and SetModifierMapping requests. This table is a shared resource and requires conventions.
A client that needs to use one of the preassigned modifiers should assume that the modifier table has been set up correctly to control these modifiers. The Lock modifier should be interpreted as Caps Lock or Shift Lock according as the keycodes in its controlling set include XK_Caps_Lock or XK_Shift_Lock.
A client that needs to use an extra modifier (for example, META) should do the following:
| - | If there is a keycode with XL_Meta_L in its set of KeySyms, add that keycode to the set for the chosen modifier. |
| - | If there is a keycode with XL_Meta_R in its set of KeySyms, add that keycode to the set for the chosen modifier. |
| - | If the controlling set is still empty, interact with the user to select one or more keys to be META. |
There is no good solution to the problem of reclaiming assignments to the five nonpreassigned modifiers when they are no longer being used.
When a client succeeds in performing a SetModifierMapping request, all clients will receive MappingNotify(request==Modifier) events. There is no mechanism for preventing these events from being received. A client that uses one of the nonpreassigned modifiers that receives one of these events should do a GetModifierMapping request to discover the new mapping, and if the modifier it is using has been cleared, it should reinstall the modifier.
Note that a GrabServer request must be used to make the GetModifierMapping and SetModifierMapping pair in these transactions atomic.
The X protocol provides explicit RGB values which are used to directly drive a monitor, and color names. RGB values provide a mechanism for accessing the full capabilities of the display device, but at the expense of having the color perceived by the user remain unknowable through the protocol. Color names were originally designed to provide access to a device-independent color database by having the server vendor tune the definitions of the colors in that textual database. Unfortunately, this still does not provide the client anyway of using an existing devicei-ndependent color, nor for the client to get device-independent color information back about colors which it has selected.
Furthermore, the client must be able to discover which set of colors are displayable by the device (the device gamut), both to allow colors to be intelligently modified to fit within the device capabilities (gamut compression) and to enable the user interface to display a representation of the reachable color space to the user (gamut display).
So, a system is needed which will provide full access to device-independent color spaces for X clients. This system should use a standard mechanism for naming the colors, be able to provide names for existing colors, and provide means by which unreachable colors can be modified to fall within the device gamut.
We are fortunate in this area to have a seminal work, the 1931 CIE color standard, which is nearly universally agreed upon as adequate for describing colors on CRT devices. This standard uses a tri-stimulus model called CIE XYZ in which each perceivable color is specified as a triplet of numbers. Other appropriate device independent color models do exist, but most of them are directly traceable back to this original work.
X device color characterization provides device-independent color spaces to X clients. It does this by providing the barest possible amount of information to the client which allows the client to construct a mapping between CIE XYZ and the regular X RGB color descriptions.
Device color characterization is defined by the name and contents of two window properties which, together, permit converting between CIE XYZ space and linear RGB device space (such as standard CRTs). Linear RGB devices require just two pieces of information to completely characterize them:
RGBintensity = M ![]() XYZ
XYZ
XYZ = M -1 ![]() RGBintensity
RGBintensity
If other device types are eventually necessary, additional properties will be required to describe them.
Because of the limited dynamic range of both XYZ and RGB intensity, these matrices will
be encoded using a fixed point representation of a 32-bit 2s complement number scaled by 227,
giving a range of-16 to 16-![]() , where
, where ![]() = 237.
= 237.
These matrices will be packed into an 18 element list of 32 bit values, XYZ RGB matrix first, in row major order and stored in the "XDCCC_LINEAR_RGB_MATRICES" properties (format = 32) on the root window of each screen, using values appropriate for that screen.
This will be encoded as:
XDCCC_LINEAR_RGB_MATRICES property contents
| Field | Type | Comments |
| M0,0 | INT32 | Interpreted as a fixed point number -16 |
| M0,1 | INT32 | |
| . . . | ||
| M3.3 | INT32 | |
| M-1 0,0 | INT32 | |
| M-1 0,1 | INT32 | |
| . . . | ||
| M-1 3,3 | INT32 |
XDCCC provides two representations for describing the conversion between RGB intensity and the actual X protocol RGB values:
| 0 | RGB value/RGB intensity level pairs |
| 1 | RGB intensity ramp |
In both cases, the relevant data will be stored in the "XDCCC_LINEAR_RGB_CORRECTION" properties on the root window of each screen, using values appropriate for that screen, in whatever format provides adequate resolution. Each property can consist of multiple entries concatenated together, if different visuals for the screen require different conversion data. A entry with a VisualID of 0 specifies data for all visuals of the screen that are not otherwise explicitly listed.
The first representation is an array of RGB value/intensity level pairs, with the RGB values in strictly increasing order. When converting, the client must linearly interpolate between adjacent entries in the table to compute the desired value. This is to allow the server to perform gamma correction itself and encode that fact in a short 2 element correction table. The intensity will be encoded as an unsigned number to be interpreted as a value between 0 and 1 (inclusive). The precision of this value will depend on the format of the property in which it is stored (8, 16 or 32 bits). For 16 and 32 bit formats, the RGB value will simply be the value stored in the property. When stored in 8-bit format, the RGB value can be computed from the value in the property by:
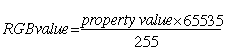
Because the three electron guns in the device may not be exactly alike in response characteristics, it is necessary to allow for three separate tables, one each for red, green and blue. So, each table will be preceded by the number of entries in that table, and the set of tables will be preceded by the number of tables. When 3 tables are provided, they will be in red, green, blue order.
This will be encoded as:
XDCCC_LINEAR_RGB_CORRECTION property contents for type 0 correction
| Field | Type | Comments |
| VisualID0 | CARD | Most significant portion of VisualID |
| VisualID1 | CARD | (exists iff property format is 8) |
| VisualID2 | CARD | (exists if property format is 8) |
| VisualID3 | CARD | Least significant (exists if property format is 8 or 16) |
| type | CARD | 0 for this type of correction |
| count | CARD | number of tables following (either 1 or 3) |
| length | CARD | number of pairs - 1 following in this table |
| value | CARD | X Protcol RGB value |
| intensity | CARD | Interpret as a number 0 <= intensity <= 1 |
| ... | ... | Total of length+1 pairs of value/intensity values |
| lengthg | CARD | number of pairs - 1 following in this table (iff count is 3) |
| value | CARD | X Protocol RGB value |
| intensity | CARD | Interpret as a number 0 <= intensity <= 1 |
| ... | ... | Total of lengthg+1 pairs of value/intensity values |
| lengthb | CARD | number of pairs - 1 following in this table (iff count is 3) |
| value | CARD | X Protocol RGB value |
| intensity | CARD | Interpret as a number 0 <= intensity <= 1 |
| ... | ... | Total of lengthg+1 pairs of value/intensity values |
Note that the VisualID is stored in 4, 2, or 1 pieces, depending on whether the property format is 8, 16, or 32, respectively. The VisualID is always stored most-significant piece first. Note that the length fields are stored as one less than the actual length, so that 2S6 entries can be stored in format 8
The second representation is a simple array of intensities for a linear subset of RGB values. The expected size of this table is the bits-per-rgb-value of the screen, but it can be any length. This is similar to the first mechanism, except that the RGB value numbers are implicitly defined by the index in the array (indices start at 0):

When converting, the client may linearly interpolate between entries in this table. The intensity values will be encoded just as in the first representation.
This will be encoded as:
XDCCC_LINEAR_RGB_CORRECTION property contents for type 1 correction
| Field | Type | Comments |
| VisualID0 | CARD | Most significant portion of VisualID |
| VisualID1 | CARD | (exists iff property format is 8) |
| VisualID2 | CARD | (exists iff property format is 8) |
| VisualID3 | CARD | Least significant (exists iff property format is 8 or 16) |
| type | CARD | 1 for this type of correction |
| count | CARD | number of tables following (either 1 or 3) |
| length | CARD | number of elements - 1 following in this table |
| intensity | CARD | Interpret as a number 0 <= intensity <= 1 |
| ... | ... | Total of length+1 intensity elements |
| lengthg | CARD | number of elements - 1 following in this table (iff count is 3) |
| intensity | CARD | Interpret as a number 0 <= intensity <= 1 |
| ... | ... | Total of lengthg+l intensity elements |
| lengthb | CARD | number of elements - 1 following in this table (iff count is 3) |
| intensity | CARD | Interpret as a number 0 <= intensity <= 1 |
| ... | ... | Total of lengthb+1 intensity elements |
This document provides the protocol-level specification of the minimal conventions needed to ensure that X Version 11 clients can interoperate properly. This document specifies interoperability conventions only for the X Version l1 protocol. Clients should be aware of other protocols that should be used for better interoperation in the X environment. The reader is referred to X Session Management Protocol for information on session management, and to InterClient Exchange Protocol for information on general-purpose communication among clients.
The X Consortium maintains a registry for certain X-related items, to aid in avoiding conflicts and to aid in sharing of such items. Readers are encouraged to use the registry. The classes of items kept in the registry that are relevant to the ICCCM include property names, property types, selection names, selection targets, WM_PROTCOLS protocols, ClientMessage types, and application classes. Requests to register items, or questions about registration, should be addressed to
Electronic mail will be acknowledged upon receipt. Please allow up to four weeks for a formal response to registration and inquiries.
The registry is published as part of the X software distribution from the X Consortium. All registered items must have the postal address of someone responsible for the item, or a reference to a document describing the item and the postal address of where to write to obtain the document.
| Home |
|---|
| Contents | Chapter 3, Part 1 | Next Chapter |